Cybersecurity attacks are on the rise, and governments are an all-too-common target. One study found 60% of cyberattacks that occurred from January to June of 2019 targeted governments. Of the “successful” cyberattacks during that period, 70% were directed at governments.
Although many government breaches go unreported by the media, some have received attention:
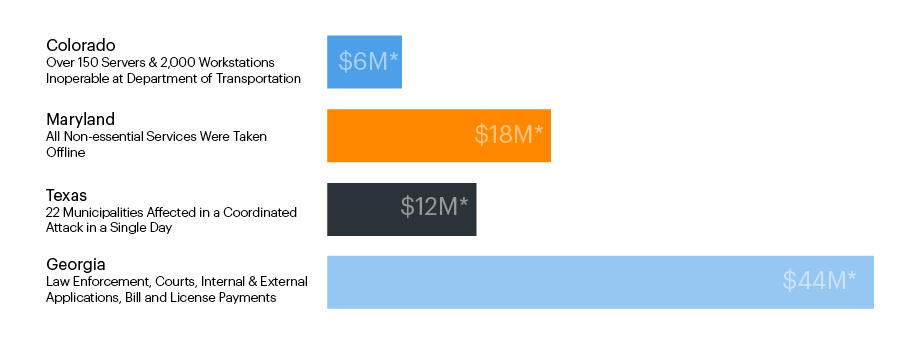
*Values representative of reported hard dollar losses as a result of cyber breaches. Soft dollar costs are not reflected in this graph.
These cyberattacks on government cost taxpayers millions of dollars and countless lost time by staff, but they also have the potential to expose sensitive citizen information, such as personally identifiable information (PII) and protected health information (PHI). Both are common data hosted on government systems and third-party cloud solutions.
State and local governments have begun to adopt policies that require third-party cloud solutions to meet some level of security threshold. However, less than 3% of state and local governments have practices in place to validate the security of third-party cloud solutions.
Securing Government Data and Systems
As governments work to secure their systems, they cannot ignore the potential risks exposed when working with unsecured cloud vendors. A recent study examined reports of data breaches in 2018 and found that “61% of U.S. data breaches occurred as a result of unsecured third-party cloud solutions.”
The federal government took action to address this serious problem and developed FedRAMP, the Federal Risk and Authorization Management Program. This program was created for the sole purpose of verifying a cloud provider’s cybersecurity posture. FedRAMP’s mission is to “simplify security for the digital age by providing a standardized approach to security for the cloud.”
With FedRAMP, a third-party assessment organization (3PAO) is used to verify a vendor’s claim that they meet best practices based on the National Institute for Standards and Technology (NIST) Cyber Security Framework. To be FedRAMP Authorized, a vendor must have a federal contract of a certain threshold. For a federal agency to contract with a cloud service, the vendor must be FedRAMP Authorized.
State governments are also beginning to explore how to address cybersecurity and cloud solutions. Many government organizations incorporate requirements in their RFPs and contracts that require vendors to meet the NIST Cyber Security Framework. However, less than 3% of the time do states verify that vendors comply with the requirement.
As many states grapple with how to manage this risk and the need for verification, a few states are taking steps. Virginia took the largest step in protecting their cybersecurity with the creation of CyberVirginia, an agency similar in nature to FedRAMP. Other states, such as Tennessee and Texas, have contracted with 3PAOs to verify NIST compliance of certain cloud providers. How states will verify vendor compliance with NIST standards is the question of the day.
Considerations for State and Local Government
1. States’ Cyber Risk Increases with Each Unverified Cloud Award.
States can reduce unnecessary risks by moving toward a “Trust but Verify” contracting approach with each new contract awarded.
2. Internal Accreditation Exposes States.
Utilizing a 3PAO accreditation provides expert oversight to mitigate the risk of protests for states.
3. Budget and Resource Allocation Prevent Verification.
Rather than create 50 unique verification methods, there could be potential for states to find cost savings and efficiencies by working together through a consortium which could leverage 3PAOs that can validate providers and acceptance of those credentials by partner states.
Our team is available to assist states and state organizations as they work to find the most efficient process for ensuring NIST compliance and a safer cyber environment for all. Contact us to learn more about how our cybersecurity experts can help your organization.





