The National Institute of Standards and Technology Special Publication (NIST SP) 800-53 launched Revision 5, also known as “Rev. 5,” in 2020. Since then, organizations like FedRAMP and StateRAMP have been working towards implementing the new security standard. When comparing NIST 800-53 Rev. 4 vs. Rev. 5, Rev. 5 introduces tailored considerations for cloud environments, addresses unique supply chain risks, and incorporates advancements in technology. To best align with today’s modern threat landscape, the control requirements have been changed through control text, updated parameters, and control discussion criteria. There have also been approximately 90 controls that were withdrawn and incorporated into other control requirements or implementation language, allowing the controls to be comprehended more easily.
David Resler, Director of Information Security at Knowledge Services, and Noah Brown, Chief Information Security Officer at Knowledge Services, discussed the NIST 800-53 Rev. 4 vs. Rev. 5 transition in its entirety. Discover the best practices for navigating this transition and gain clarity on the newest controls in Rev. 5.
Control Revisions, Considerations, and Prioritizations
One of the biggest introductions in Rev. 5 is the Supply Chain Risk Management (SCRM) control family which included new, critical control requirements. These new requirements streamline supply chain controls, enhance processes for supplier assessments and reviews, and foster more efficient supply chain management. SCRM aspects are integrated across multiple control families to safeguard critical system components and business offerings within complex infrastructures. These controls ensure security and privacy requirements are addressed accordingly.
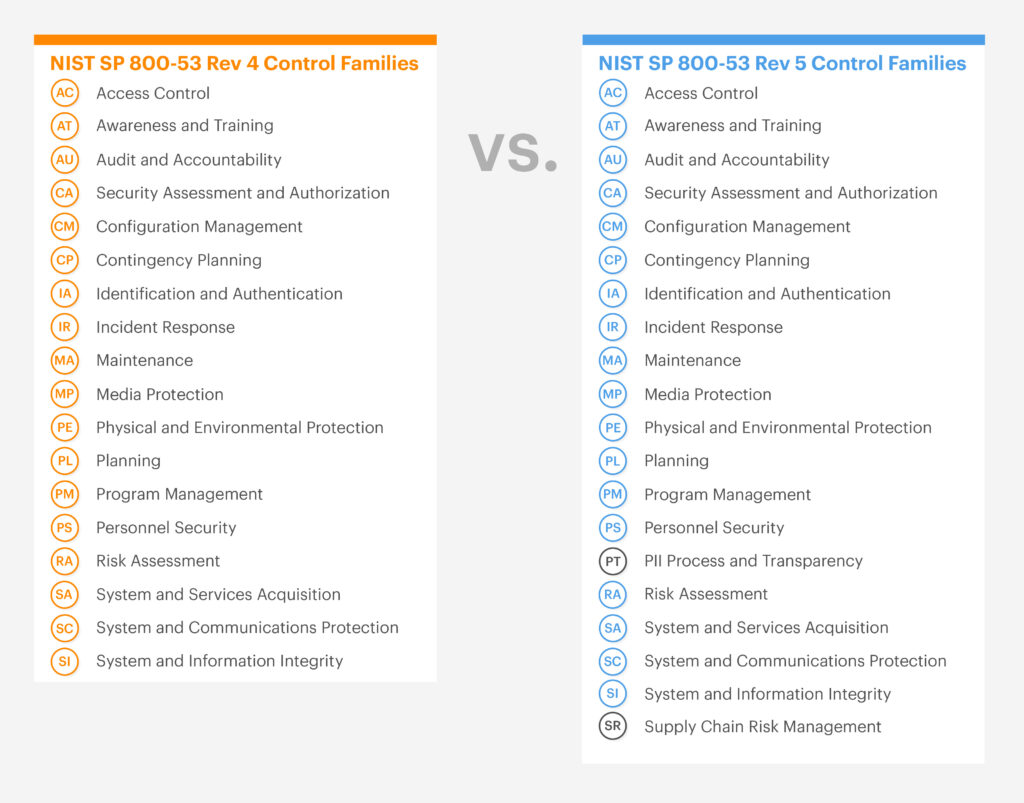
The SR-2 control requirement, which involves building out the SCRM plan, can present a strong learning curve for many providers, especially those new to working in the cloud space. Successfully navigating this transition requires implementing robust checks and balances within the supply chain, alongside efficient documentation of processes. Given the introduction of new control language, referring to NIST guidelines for SCRM and utilizing available templates can greatly assist providers in navigating this area. StateRAMP has also updated its requirements to align with Rev. 5 and has provided available templates as a reference point.
Gap Assessment Prioritization
All providers should conduct a gap assessment to effectively allocate resources. A significant obstacle to overcome is discovering the current security posture of the company and how to improve it. For implementing new control requirements, providers should follow the MITRE impact scoring. This model shows which control requirements will have the largest impact on your security posture. Upon completion, the gap assessment will provide a look into what controls are already in place and which ones need to be worked on.

Guidance for a Seamless Transition
Companies that currently follow the NIST 800-53 framework need to update to Rev. 5 regardless; it is just a matter of when. Although not a minor update, Rev. 5 builds upon the foundation established in Rev. 4. Therefore, the workload completed for the Rev. 4 transition is still applicable and puts companies a step ahead for adopting Rev. 5.
Providers in the process of obtaining StateRAMP certification can continue to utilize Rev. 4 documentation as they prepare for the transition to Rev. 5, until October 1, 2024.
First Steps
At first, it may seem daunting to implement the new control requirements, but with the right guidance, it’s a straightforward process. An initial step for companies involves conducting research and collaborating with the development team to explore available libraries. From gaining a Software Bill of Materials (SBOM), companies gain clarity on what is being incorporated into the software builds by reference. This allows companies to stay ahead and know what is in the software.
Engage with IT Leaders and 3PAOs
Along with the updates to Rev. 5, the hardening program for servers, such as the infrastructure components, has been changed from the Center for Internet Security benchmarks to the Defense Information Systems Agency (DISA) Security Technical Information Guides (STIGs). By engaging with IT leaders, they can ensure the STIGs are properly implemented. The earlier you can involve information security, the smoother the Rev. 5 transition will be. This allows for an open dialogue between the development and IT staff, ensuring all stakeholders are on the same page.
Community Resources
Companies navigating the NIST 800-53 Rev. 4 vs. Rev. 5 transition could greatly benefit by networking with industry leaders who are familiar with this process. Leveraging LinkedIn offers an excellent opportunity to connect with industry leaders through various groups and networks. These community groups act as a valuable resource for understanding the best transition tools and practices to utilize. Industry leaders understand how licensing costs and software can add up quickly and how certain decisions will impact your company in the long term. Gaining this critical insight benefits companies from a security risk and financial perspective, preventing long-term resource constraints.
“I cannot stress the importance of community to enable Rev. 5. These (LinkedIn) communities are very valuable in driving innovation and compliance within all organizations. When security practitioners work together, regardless of if we are competitors or in different industries, it helps make everyone more secure.”
– David Resler, Director of Information Security at Knowledge Services
Risk Mitigation
With a transition this significant, there can be some discrepancies that come along. When providers conduct an internal assessment, they may not be aware of some control findings related to a specific control. While there may be pressure from leadership to quickly implement solutions, providers may not fully understand the controls being implemented the way a consultant or advisor would. This can lead to missing out on necessary processes. A critical obstacle for larger organizations is the alignment of priority for all stakeholders. The larger the organization, the harder it is to implement new requirements and pivot to control requirements to manage that risk.
To provide companies with further clarity in this transition, NIST has published significant documentation on specific control guidance.
Importance of Employee Training
The two most common causes of a breach are phishing and unpatched software. When cybercriminals leverage these two together, the result is often a breach for large and small organizations alike. Implementing security awareness training at all levels is critical since this is where security starts. Employees should be trained on identifying the differences between a phishing attempt and spam. They should also be instructed how to properly handle a phishing attempt when one happens. Education and training for stakeholders and leadership are crucial. The executives at any organization need to have buy-in on this transition and understand what is at stake if training is not properly enforced. To successfully execute employee awareness training, the training should be a continuous effort and kept at the forefront of every employee’s mind.
Properly Integrate Third Parties
Many larger breaches stem from third-party systems that have access to an organization’s environment. If an organization is looking for a cost-effective solution to move to a third-party party, it may be at the cost of compliance. Partnering with a third-party party that does not meet all compliance requirements sounds cost-effective, but larger issues could develop for the organization. Companies must prioritize education on what a third-party party partnership could mean financially for the organization. For those that have third-party party partnerships, it is important to validate that the suppliers meet the same security standards as your product or service. Such validation strengthens the cyber posture of an organization while driving the adoption of Rev. 5 in its entirety.
Connect with IT Leaders Today
Transitioning from Rev. 5 is a heavy lift but a straightforward process with proper guidance. Networking with industry leaders enables companies to adopt best practices and receive expert advice, ensuring comprehensive adherence to security and privacy control requirements. If you’d like to learn more about your organization can reach your business goals, connect with our cybersecurity consultants today for a seamless Rev. 5 transition.





